With the rise in eCommerce, hackers are targeting more eCommerce websites than ever. But how do hackers find your eCommerce website? Is it targeted? Is it random?
Well, it’s a little of both, actually.
Like POS attackers, eCommerce data thieves often look for data that’s an easy target. This typically includes eCommerce websites using popular open source languages, code libraries, or shopping cart software. If attackers find a vulnerability they can exploit, they will search out any website using that language, library, or software and use that exploit to steal data, inject malware, or take stealth control of the system.
Of course, attacks are not always the result of a random search. A company may be seen as a high value target. High profile companies usually experience an increased rate of intentional targeting.
How Hackers Find Your eCommerce Website
There are many ways, really. Here are a few of the more common methods:
Open-source attacks
These attacks are one of the most popular methods because they are usually relatively easy to identify and exploit. The attacks are against companies that use applications with open-source code and tools. Many attackers view these type of websites as “low hanging fruit.”
Many companies choose to use open-source tools to build their websites because they’re free and allow fairly easy customization by low cost, entry level programmers. Unfortunately, somewhat novice programmers often make configuration and code changes, not fully realizing the security implications of these changes.
Due to the open-source nature of many eCommerce platforms and web programming languages, hackers, pen testers and white hat researchers are constantly exploring, testing, and publishing discovered vulnerabilities and the methods that were used or might be used to exploit the vulnerability. Skilled hackers may even publish easy-to-use tools that wannabe hackers and script kiddies frequently use to compromise vulnerable websites.
Two of the more popular open-source tools targeted by hackers are WordPress and Magento. These two tools are attractive to attackers because they’re relatively simple for businesses to set up and customize, while also having a fairly complex code base that provides many potential attack vectors.
- Magento is an open source, off-the-shelf shopping cart used by many thousands of businesses.
- WordPress is a content management system (CMS) but also has eCommerce capabilities.
This doesn’t mean these tools should be avoided. It simply means they can be more prone to vulnerabilities since they are open source; therefore, greater care should be taken when configuring. Also, remember that at the same time hackers are discovering vulnerabilities, there are also people working to patch them up. That’s why it’s absolutely critical to stay up to date on security patches if you use these types of website tools.
As a best practice, you should make sure you work with trusted experts and recommended plug-ins when working with any open source system. Experts at Magento or in the WordPress community can help guide you here.
Third party plugins
Additional functionality is frequently added to open-source applications such as Magento and WordPress. Attackers will occasionally create and publish new plugins or modify other open-source plugins. These plugins appear to be helpful and harmless but contain intentional or unintentional vulnerabilities or even hidden backdoors. Users should be especially cautious when implementing third party plugins.
Zero-day attacks
Zero-day attacks can happen when attackers become aware of a vulnerability before the vendor and begin exploiting the vulnerability. Vendors sometimes have to scramble to get a “hot fix” out to users. But in some cases, it can take several months to properly fix a vulnerability. Between that time and the time it’s discovered and patched, your website could be vulnerable to hackers.
Attacks in PHP and other web languages
PHP (hypertext preprocessor) and similar open-source scripting languages are used for web development and backend application programming. A problem with open-source languages is hackers know so much about it and can occasionally find vulnerabilities in the most mundane lines of code. Every time a new language or a new version of the language is released, hackers go into overdrive, looking to exploit new vulnerabilities before they are discovered and patched by the support community or developers.
Input field code injection
Most people running a website have heard of SQL injection attacks. This methodology continues to be a hacker favorite, despite how relatively easy it is to prevent. An input field is the area on a web form that asks for specific information (date, phone number, credit card number, etc.). But input fields aren’t the only method of sending data to a webserver. The URL line often contains input fields easily changed by an attacker. When input fields aren’t properly sanitized, attackers can use certain coding characters to cause the backend programing language to execute malicious code instead. Even if fields are sanitized, hackers may still ferret out useful information that can be used to gain additional knowledge by the way the server responds to unusual input data.
Buffer Overflow Attacks
Even though incoming data may be sanitized, if not also validated for things like correct size and data type expectations, hackers may use a sneaky trick such as submitting large amounts of data to a website causing the webserver to possibly malfunction. If the malfunction is severe enough, hackers may be able to exploit that malfunction to gain control of the webserver.
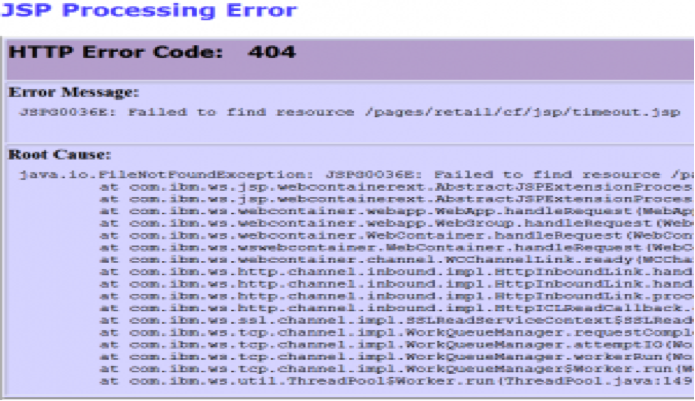
Error Message Reconnaissance
When most users get an error message like the one below, they quickly hit the back button.
But to a skilled hacker, this can be a gold mine of information about the server. Websites are often loaded with these types of error messages, and hackers can make use of them to gain valuable knowledge that may be used to later create a successful breach.
To combat this risk, make sure all data is both sanitized and validated. Sanitizing is removing any programmatic characters contained in any incoming data fields. Programmers sometimes forget to sanitize and validate data from sources like their own database, thinking that since they control the data source, it does not require time consuming sanitation and validation. But if an attacker compromises a database by a web application, the attacker can input unrestricted data into the database. When the website uses the corrupted data in the database, a clever hacker can open up the entire website and webserver to compromise. Again, sanitization is the removal of possible malicious characters contained within any incoming data stream. Validation ensures the specific information is supposed to be there, is the right type of data and the expected amount of data.
What to do to prevent getting breached
The nice thing is at the same time hackers are finding vulnerabilities in open source resources, there are also numerous people finding and fixing problems. The key is staying updated on security and following all recommended best practices. Here are several of the most critical best practice recommendations concerning running a secure website:
- Install and use a file integrity monitoring (FIM) program: File Integrity Monitoring watches for any changes to individual files or all files within specified directories. If an attacker is successful at modifying a file, FIM can alert IT staff who can respond immediately and remediate the breach. Too often companies install FIM but alerts go to a seldom checked email account or to a rarely reviewed log file. Many FIM systems now allow alerts to be sent via text message to both IT staff and a manager so that incidents can be addressed quickly and with full accountability.
- Keep up to date on patches: Security patches and hot fixes should be installed immediately—upon publication if possible, but in no less than 24 hours. Many applications send alerts when new patches or releases are available. Policies should be in place to enforce immediate patch updates.
- Use intrusion detection systems: Intrusion detection systems (IDS) monitor logs looking for evidence of a breach. IDS alerts should be addressed as quickly as possible.
- Use intrusion prevention systems: Like IDS, intrusion prevention systems (IPS) monitor traffic in [near] real-time watching for evidence of real time attacks and will then generate an alert when suspicious activity is detected.
- Avoid exposing vulnerabilities: While customizing your website and tools is great for business, it can lead to vulnerabilities. Programmers should be extremely careful when altering code. Code review should be conducted regularly to check for security holes and unintended consequences..
- Sanitize and validate input fields: As mentioned earlier, all incoming data should be sanitized by removing potentially dangerous characters, and validated to ensure that the data meets correct type and size constraints.
- Use staging or development servers to test new code and 3rd party plugins: Website changes should always be tested and reviewed in a non-production environment along with any plugins and outsourced development.
One of the biggest issues with eCommerce security is the malefactors have ample time to look for and exploit vulnerabilities. They only need to be right once to have a successful breach. IT staffs, pen testers, programmers and security researchers all have to be right all of the time. This is of course impossible and data breaches will occur from time to time. If you hack-proof something, the world will produce a better hacker. Does that mean the situation is hopeless? Not at all!
Remember, hackers generally go after the low hanging fruit and there is plenty of it out there. Implementing a handful of simple, reasonable precautions and security strategies can quickly raise your eCommerce environment to relative safety of higher branches.
Of course, the more valuable your eCommerce environment appears to data thieves, the more diligent your security efforts must be. The number one best practice that must be followed is to never believe you are finished with your security. What may be an uber-secure application, webserver or programming code today could become tomorrow’s Achilles’ heel.
Business owners, IT staff, developers and management must stay up to date and well trained on security issues in order to act proactively and respond effectively. This often requires an investment of precious time and resources, and the return on that investment can easily be overlooked when things proceed smoothly. But as thousands of businesses that have born the savage mental, moral, and financial stress of a serious security breach can all attest, none of them—in hind sight—ever wished that they had invested less.
David Ellis (GCIH, QSA, PFI, CISSP) is Director of Forensic Investigations at SecurityMetrics with over 25 years of law enforcement and investigative experience.
Aaron Willis (CISSP, QSA, PFI) is a Forensic Analyst at SecurityMetrics, and has over 15 years of diverse experience in all aspects of IT security, business intelligence, data mining, SaaS consulting, and programming.
SecurityMetrics (securitymetrics.com) is a global leader in payment data security for all business sizes, and as an Approved Scanning Vendor and Qualified Security Assessor, has tested over 1 million payment systems for data security and compliance. Among other things, SecurityMetrics offers PCI audits, PA-DSS audits, consulting, mobile device vulnerability scanning, penetration testing, security appliances, data discovery tools, and forensic analysis.
Frequently Asked Questions
What is payment fraud?
Payment fraud is when a cybercriminal completes a false or illegal transaction, depriving the victim of funds, property, interest or sensitive information.
What is fraud prevention?
Fraud prevention involves using tools to help analyze customer data and purchase behavior on every transaction to identify and stop fraudulent orders, and to reduce false positive rates.
How does BlueSnap help with protecting against fraud?
BlueSnap partnered with Kount, a leader in fraud prevention services, to analyze customer data and behavior on every purchase. We offer three fraud prevention services levels to serve your unique needs. Learn more here.
What are payment regulations?
There are six key regulatory categories businesses must consider and adhere to when conducting any financial transaction:
- Payment network policies: These include any rules, regulations, guidelines or specifications put forth by payment networks, including EFT networks and Credit Card Associations.
- Data privacy: These regulations cover the rights given to individual data subjects concerning the personal data being stored (information like an individual’s name, email, location, online identifier, IP address, home address, etc.), including the right to prior notification of what the data is being used for, how it will be processed and when it will be deleted.
- Consumer security: These regulations protect consumers from fraud and theft, such as the Revised Directive on Payment Services (PSD2), enacted by the European Parliament, which requires Strong Customer Authentication (SCA) via three levels of identification for every transaction, from card number confirmations to texts with authorization codes.
- Payment Card Industry Data Security Standards: Payment Card Industry (PCI) is a Data Security Standard (DSS), which is a set of requirements established by the major card companies to ensure that all businesses that process, store and/or transmit credit and debit card information maintain a secure environment. These standards help to defend against cyber-attacks, data hacks and other security breaches, which can result in extensive costs associated with loss of business, credit monitoring, post-breach audits and security updates.
- Tax collection: Tax responsibilities for businesses depend on a variety of factors such as the sales revenue, transaction volume and the location in which sales occur. In addition to the specific local tax laws, the payment model under which your business operates also has an impact.
- IT security: These regulations ensure that businesses are protected against hackers, cybersecurity regulations have been drafted to cover elements including data center redundancy, data storage, data recovery and other security investments.